Identity Relationship Management
In my recent blog, I listed “Relationships” as a major theme addressed during the Catalyst conference. In the art and science of Identity Management, relationships between Identities are what deliver business value. Perhaps the monikor for our industry should be Identity Relationship Management.
In the discipline of database design, Entity Relationship diagrams are used to diagram database schemas. In a database, neither entity nor relationship is complete without the other. It is the definition of relationship between data elements that adds value- hence the pervasive utility of the relational database.
A simple “Identity Relationship Diagram” (my term) helps to illustrate the concept. Identities are shown in boxes; relationships are shown as arrows.
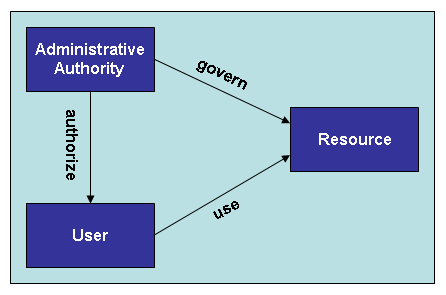
If we think of why Identity Management has business value, the value of Relationships become apparent. When a user is granted login privileges to a resource (e.g. application, system), relationships are brought into play on at least three levels:
- A governance relationship between one or more administrative authorities and the resource
- An administrative relationship between such authorizing parties and the user to whom privileges are granted
- The granted relationship between the user and the resource
At the Catalyst conference, Randall Gamby of the Burton Group observed that “workflow deals with relationships  between people.” Indeed, automated workflow processes are used to implement the first two relationships listed above.
In a real sense, such workflow processes constitute the business policy governing the third relationship. In his Catalyst conference presentation, Ken Weiss of Charles Schwab commented that “policies define how Identities are permitted to access resources.”
Of course, this is just a simple example. Many more Identity Relationships can be easily listed – consumer to vendor, reader to news source, participant to online community, to name a few. Value accrues to each party in such relationships after access is granted and relationships are consumated. Establishing trust, authenticating identities, authorizing access and enabling exchange of information, goods and services are all part of consumating such relationships. Identity Management is at the heart of establishing such secure relationships. Jarrod Jasper of GM observed at Catalyst: “”How long does it take to enable a desired relationship so someone can get to work?” Perhaps I could paraphrase further: “How long does it take to enable the exchange of value between Identites?”
The understanding of Identity Relationships helps us to understand the business value that accrues when Identity Management is implemented. As I discussed with Nick Nikols of the Burton Group at the Catalyst Conference, the tools to manage Identities are becoming mature and productive, but tools to manage relationships should become more complete as the Identity Management market continues to advance.
In the mean time, I’ll ponder some more on how to use IRD’s (Identity Relationship Diagrams). I think better in pictures.
Tag: Identity

[Trackback] 野æ‘ç·åˆç ”究所ã®é¦¬å ´ã•ã‚“ãŒæ›¸ã„㟠IdM ã®è§£èª¬ ã«æ¬¡ã®ã‚ˆã†ãªè¨˜è¿°ãŒã‚ã‚‹:
アイデンティティã¨ã¯,
å˜ã«ãã®ãƒ¦ãƒ¼ã‚¶ãŒä½•è€…ã§ã‚ã‚‹ã‹ã‚’示ã—ãŸã‚‚ã®ã§ã¯ãªã„.
ãã‚Œã¯, 組織ã«ãŠã‘ã‚‹ãã®ãƒ¦ãƒ¼ã‚¶ã®å½¹å‰²ã¯ä½•ã‹,
ãã®ãƒªã‚½ãƒ¼ã‚¹ã‚„æƒ…å ±ã«å¯¾ã—ã¦ãã®ãƒ¦ãƒ¼ã‚¶ã¯ä½•ãŒã§ãã¦ä½•ãŒã§ããªã„ã®ã‹ã¨ã„ã†,
利用ユーザーã¨ä¼æ¥ã‚·ã‚¹ãƒ†ãƒ ã¨ã®é–¢ä¿‚を定義ã—ãŸã‚‚ã®ã§ã‚ã‚‹ .
アクセス権é™ç®¡ç†ã®æ–°ã—ã„考ãˆæ–¹ã€Œã‚¢ã‚¤ãƒ‡ãƒ³ãƒ†ã‚£ãƒ†ã‚£ãƒžãƒã‚¸ãƒ¡ãƒ³ãƒˆã€
…