Verizon 2013 Data Breach Investigation Report: Assume You’re Breached
The annual Verizon Data Breach Investigation Report  was recently published. The opening statement really tells the story:
Perhaps more so than any other year, the large scale and diverse nature of data breaches and other network attacks took center stage. But rather than a synchronized chorus making its debut on New Year’s Eve, we witnessed separate, ongoing movements that seemed to come together in full crescendo throughout the year. And from pubs to public agencies, mom-and-pops to multi-nationals, nobody was immune. As a result—perhaps agitated by ancient Mayan doomsday predictions—a growing segment of the security community adopted an “assume you’re breached†mentality. (emphasis added)
The post I made a few minutes ago about 94% of healthcare companies suffering a breach is certainly in line with this attitude.
What is one to do? Â I liked the way Verizon concluded the report.
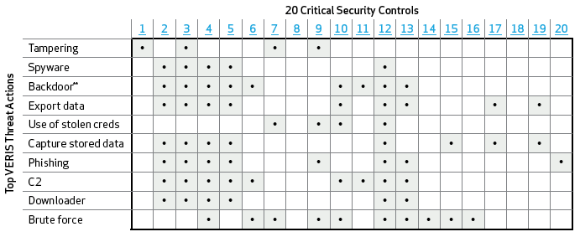
We worked with the recently formed Consortium for Cybersecurity Action (CCA) and mapped the most common [VERIS] threat action varieties to their Critical Security Controls for Effective Cyber Defense … Most organizations should implement all 20 of the Critical Security Controls to some level.
The following diagram shows the Critical Security Controls mapped to the top VERIS Threat Actions:
Enterprises must implement comprehensive, end-to-end security. Â It’s not easy, but we must do it.
Â
Â