Identity
Author:
Mark Dixon
Thursday, August 27, 2009
4:49 pm
 I enjoyed reading Felix Gaehtgens’ recent article entitled "Quick Wins in Identity Management." The essence of his post is summarized in his second paragraph:
I enjoyed reading Felix Gaehtgens’ recent article entitled "Quick Wins in Identity Management." The essence of his post is summarized in his second paragraph:
With the current squeeze on cost and corporate spending, many IT departments find themselves in a true quagmire. On one hand, the IT industry is focusing on efficiency like never before – elaborating new approaches and processes to increase efficiency and do more with less. Governance and risk management is a big issue whose lack has greatly contributed to the current crisis. IT is under scrutiny to be more of a business enabler and less of a cost center. All of this requires change, new technology, and strategic vision. But as IT spending is reduced or even capped, this creates a Catch 22 situation. Under pressure, some IT departments try for more tactical approaches that can eventually be expanded into a broader strategy. Quick wins are needed to get there.
It is great to know that in prevailing Identity Management thought, the Quick Win concept is still valid. Back in June, 2005, I authored a post entitled "Quick Wins for Identity Management," highlighting "Sun’s Quick Win philosophy." In that article, I proposed:
The value of a quick win project should not be underestimated. A number of advantages can accrue:
- Measurable results are quickly demonstrated
- Project momentum is maintained for future phases
- The likelihood of continual sponsorship is increased
- The system architecture is progressively validated
- Configuration components are more easily reused
- Impact on the enterprise is more easily understood
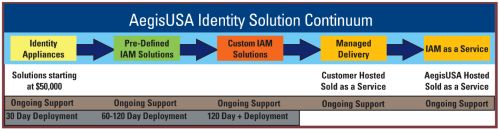
It is interesting, and not altogether coincidental, that a post I wrote earlier today featured the AegisUSA announcement of "Identity Appliances" to reduce entry costs and accelerate time to value. The AegisUSA offering is yet another validation that the Quick Win philosophy really does work.
So, let me leave you with Felix’s final words:
As usual, those who take a good long-term view are usually rewarded most in the long run. But when strategic initiatives are out, and the thinking is tactical, the above mentioned areas have shown the potential for quick wins. These quick wins have additional benefits because they can be everybody, but that cannot be an excuse to do nothing – those who are smart and creative will be able to push ahead in front of others. Hopefully these ideas will help you delivering value in these tough times.
… and mine, from the June 2005 article:
We encourage you to make this your philosophy: Segment your Identity Management project into manageable parts. Focus your attention first on the most urgent, most beneficial, most quickly implemented areas of the entire project scope. Drive directly to those areas where you will experience a quick win.
Ladies and Gentlemen, start your engines.
Technorati Tags: Identity, IdentityManagement, DigitalIdentity, QuickWins