Identity
Author:
Mark Dixon
Wednesday, August 1, 2012
9:47 pm
This afternoon, I took an intriguing romp through several recent articles about personal data, clouds and operating systems – somewhat following on my recent exploration of Life Management Platforms, which fall into the same general category. I really like the emphasis on the term Personal. True personalization implies that I am able to leverage my identity to get more and more value from my online experience.
I started my little exploration with Drummond Reed’s recent post, Social, Local, Mobile, Personal, which led me to two posts on the Respect Network blog:
These posts in turn led me to an intriguing white paper, From Personal Computers to Personal Clouds, The Advent of the Cloud OS, written by industry luminaries Craig Burton, Scott David, Drummond Reed, Doc Searls, and Phil Windley,
A few items that really connected with me:
First, the following chart from Drummond’s post illustrates the progression toward a personal network or platform. That seems particularly relevant to me as Facebook, though social, is decidedly and increasingly less personal. I would very much like to see concepts such as Life Management Platforms and Personal Channels emerge to give me more control over my information and interactions with others.
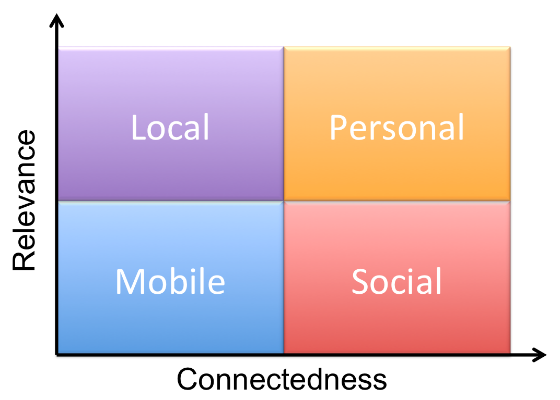
Second, I like the concept that Personal Channels provide “Volume Control” plus “Intelligent Filtering and Organization.” I have become increasingly perturbed at the level of irrelevant noise on Facebook and Twitter. To some extent, I can filter things down by using groups and lists, but it is cumbersome and very limited.
Third, the concept of a cloud operating system is powerful. The ability to have a COS to handle services like Identity, Program Execution, Data Abstraction and Communication will enable much innovation and will be necessary to really deliver functionality like Life Management Platforms and Personal Channels.
However, unless someone can deliver infinite bandwidth to us all, I doubt that we will completely get away from the mobile device “calf” connected to the cloud “cow,” to borrow Craig Burton’s model. Intelligence at the personal device OS level that is uniquely positioned to provide crisp, beautiful and functional user interfaces will need to be seamlessly integrated with powerful functionality and connectivity at the COS level.
After reading and trying to understand all this innovative thinking, I bumped into an article about app.net, a project which claims to be building a “different kind of social platform”:
We’re building a real-time social service where users and developers come first, not advertisers … We believe that advertising-supported social services are so consistently and inextricably at odds with the interests of users and developers that something must be done.
It sounds like the app.net platform will not only provide a “personal channel,” but a cloud operating system of sorts, where developers can plug in interrelated applications in a standardized way. It doesn’t appear to possess all the qualities of a COS as defined in the Burton, et al, white paper, but perhaps it is a step in the right direction. I signed up as an early adopter in hopes their project gets funded.





 Today, the 11g R2 version of the Oracle Identity and Access Management platform was
Today, the 11g R2 version of the Oracle Identity and Access Management platform was 
 One of the high-value benefits of an integrated Identity and Access Management platform is the ability to leverage a unified corporate directory as the primary authentication source for database access.
One of the high-value benefits of an integrated Identity and Access Management platform is the ability to leverage a unified corporate directory as the primary authentication source for database access.