Time is Relative … and Accelerating (My Christmas Theory of Time)
 Dave Kearns just commented on a Facebook photo of me at Richfield (Idaho) High School graduation, asking, “were we ever that young?”.
Dave Kearns just commented on a Facebook photo of me at Richfield (Idaho) High School graduation, asking, “were we ever that young?”.
Great question, Dave. Â It is hard to believe, but yes, over 40 years ago, when the photo of that skinny, dark-haired earlier me was taken, I was young.
That made me think of a theory I have about the relativity of time. Â Do you remember when you were 5 years old? Â Back then, I measured years from Christmas to Christmas. Â It seemed that it took forever for another Christmas to come around.
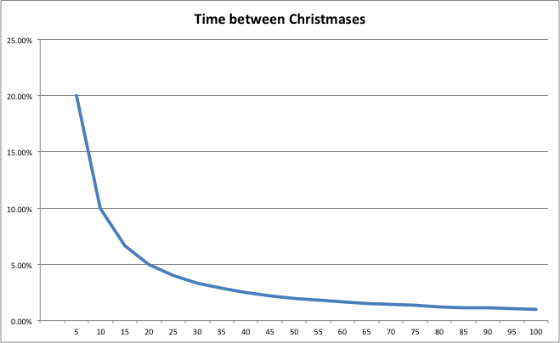
But when I was 5 years old, a full twenty percent of my life had to pass before another Christmas would come. Â Relative to my life experience, it did take a long time.
Now, however, only 1.7% of my life passes between Christmases. (You can figure out the math). And every year, the percentage becomes smaller. Â If I live long enough, the time between Christmases will approach zero.
In the mean time, I can be thankful for the fact that I really once was that young, and can revel in the current reality that my youngest daughter is now a senior in high school, having experiences akin to what I had 40 years ago, and that my grandchildren are also learning to spread their wings and fly!