Enabling Collaboration by with Social BPM
This morning, I was read a recent Oracle White Paper entitled, “Transforming Customer Experience: The Convergence of Social, Mobile and  Business Process Management.”  It gave interesting perspective on the blending of emerging paradigms – mobile and social – with the older discipline of Business Process Management.
To stay ahead in today’s rapidly changing business environment, organizations need agile business processes that allow them to adapt quickly to evolving markets, customer needs, policies, regulations, and business models. … Social and mobile business models have already contributed important new frameworks for collaboration and information sharing in the enterprise. While these technologies are still in a nascent state, BPM and service oriented architecture (SOA) solutions are well established, providing a history of clear and complementary benefits.
The key is effectively leveraging the strengths of existing, proven architectures while taking advantage of new opportunities:
The term “Social BPM†is sometimes used to describe the use of social tools and techniques in business process improvement efforts. Social BPM helps eliminate barriers between decision makers and the people affected by their decisions. These tools facilitate communication that companies can leverage to improve business processes. Social BPM enables collaboration in the context of BPM and adds the richness of modern social communication tools.
… Social BPM increases business value by extracting information from enterprise systems and using it within social networks. Meanwhile, social technologies permit employees to utilize feedback from social networks to improve business processes.
I found one use case presented in the paper to be particularly instructive. As illustrated in the following diagram,
A claims management system assigns a task to an individual claims worker with the expectation that the user will complete the task to advance the process. Of course, to accomplish this type of knowledge-based task, the individual must often engage other people within the business .
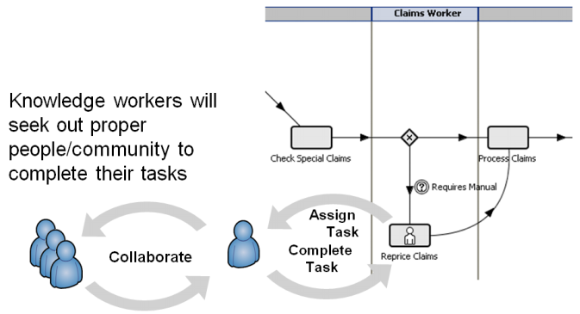
However, Social BPM enables the use of social networking tools to extend collaboration beyond the traditional enterprise boundaries, as shown in the following diagram:
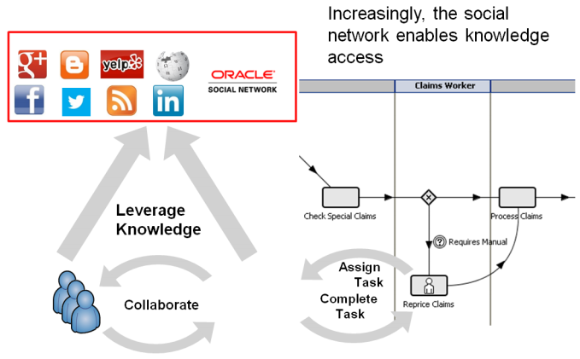
Not only can internal knowledge workers use social networking tools to find each other and share information, but also customers can interact with the process at specific steps, using mobile devices, to supply their own information into a business process. For example, a customer involved in an auto accident might upload photos taken with a cell phone into the process via a claims management app provided by the insurance company.
In order to make this all work, participants will need to use both enterprise and social identity credentials. Because they are using mobile devices, the IAM system must accommodate  mobile, social and cloud infrastructures in order to effectively use information.  This is very much in line with the principles set forth in the Gartner Nexus I addressed yesterday.