Today, I enjoyed reading T.Rob’s post, “ Do you consider your digital identity a separate self or is it identical to your real-world self?” Â I started to respond to his post as a comment, but decided to write the following post.
Back in November, 2005, I began writing a series of posts about “The Identity Map,” which was centered on a concept I called “Core Identity.”
I think this Core Identity concept goes to the heart of what T.Rob discussed – that perhaps:
identities change over time … The one place we make an effort to distinguish between a person’s identities is in the present moment. The T.Rob who exists right now is a multi-faceted, yet unique entity. I participate in many communities across many interests …
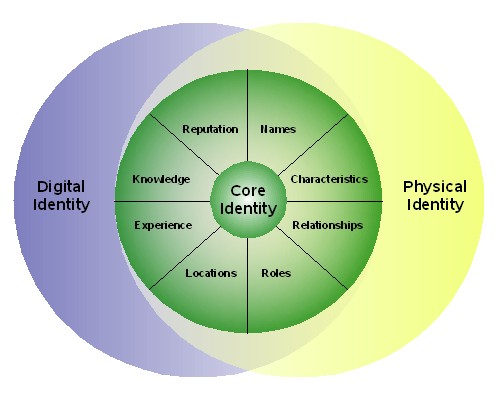
I would propose that the core of who we are does not change, but many characteristics, including both physical and mental attributes do change over time. We may possess multiple “digital identities,” or perhaps more specifically, “digital personas,” which are but subsets of the complex core identity and the myriad set of attributes surrounding that core. Â I drew this chart in November, 2005:
The remainder of this post comes from a couple of earlier posts - here and here.  Thanks, T.Rob, for triggering these memories.
—-
Core Identity is the essence of who a person is. This unique “Core Identity” can be identified or described by attributes that belong to and describe an individual. Some unique characteristics (e.g. DNA signature, footprint) are immediately measurable at birth. Others change over time.
The attributes that further identify and describe an individual are:
Names. I am known by many names. My given name is Mark. My surname is Dixon. My i-name is MarkDixon.My social security number is [wouldn’t you like to know?]. My kids call me Dad.
Characteristics. I have some measureable characteristics that don’t change – my DNA signature, my fingerprints. Others change over time – height, weight, hair color. Does IQ change? I don’t know.
Relationships. I have relationships with people, institutions and things. I am father to my children, brother to my siblings, husband to my wife. I am an employee of Sun Microsystems and an alumnus of Brigham Young University. I own a Nikon camera. I love Chinese food. I can’t stand professional wrestling.
Roles. The functions I perform in life are roles: Father, husband, Sun Identity Practice Lead, Identity blogger, Church volunteer, registered voter.
Location. When I used to travel every week, I’d tell people I claimed home addresses in Mesa, Arizona and United seat 2B. These are descriptors of physical locations, relative to different known reference points. However, my current location (latitude, longitude, elevation) will vary, dependingon where I am physically located at any moment in time.
Experience. I have experienced many things in the 52+ years of my earthly existence. I have been stabbed by a pitchfork, run for a touchdown, flown around the world and milked a cow (many times). Each experience adds uniqueness to my core identity.
Knowledge. During my existence, I have amassed much knowledge, some of it shared by many, some of it unique. Both you and I probably know the Pythagorean Theorem. You probably don’t know the names of my kids. I hope you don’t know my blog password.
Reputation. Other people and institutions say things about me, some of it good, some of it bad. The credit bureaus say I have a good credit rating. The DMV say I’m a so-so insurance risk because I’ve had a couple of tickets in the past three years – but they also say I hold a valid drivers license. BYU says I hold a BSEE degree. My wife likes me (and that is what really counts).
Â