IAM Project Governance – Cooperative Execution
Back in November 2009, I wrote a post entitled, Best Practices for the IAM/Compliance Journey that outlined 13 recommended practices to improve the probability of success in implementing IAM systems. Â One of the recommended practices was “Establish a Governance Process”:
Compliance efforts affect a broad spectrum of an enterprise. Stakeholders from many organizations, often with conflicting priorities, have vested interests in the outcomes of a compliance strategy. The governance process must provide representation from the impacted functional areas of the organization. A governance board should have appropriate representation from IT, security, audit, application owners, human resources, business process owners and applicable business associates. The board should be accountable for the project objectives and be vested with authority to make program decisions. The board should be empowered to 1) establish a statement of purpose for the program, 2) promote and give visibility to the program throughout the larger organization, 3) act as a mechanism for quickly making decisions regarding program scope, issues, and risks, and 4) monitor the program health on an ongoing basis.
This recommendation certainly still holds true. Â It refers to the type of Strategic Governance that should be an integral part of a company’s IAM strategy, ensuring that IAM technology is aligned with and supports a company’s business objectives and strategy.
However, in the past few months in my work with Oracle, I have begun to crystalize my thoughts about a more tactical kind of governance, which I call IAM Project Governance. Â This process is focused on how to make sure a specific project within the IAM journey stays on track and meets specific tactical objectives under the umbrella of the company’s IAM strategy.
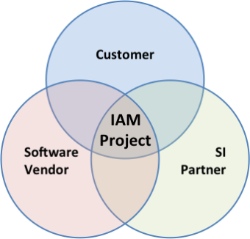
IAM Project Governance is based on four distinct, but interrelated principles in a spirit of Cooperative Execution:
Alignment
The three major participants in an implementation process – Customer, Software Vendor and Systems Integration Partner – must be aligned in project objectives,  understanding of the project plan and the project schedule.  This alignment must include executive sponsors, director and management levels, and project levels from all three parties.
Commitment
The three major participants must be uniformly committed to the project success, and be willing to work together to make it so. Â This is real commitment, of focused attention, time, effort and resources that will lead to mutual success.
Communication
Communication must be regular, articulate, candid and open. Â A regular cadence of interaction at all levels of the project leadership, from executives down throughout day-to-day project team members, must be organized executed. Â It is this type of regular communication that can nip problems in the bud by giving proper attention and allocating appropriate resources before problems fester and grow out of control.
Consistency
Implementing an IAM system takes focus, hardware and consistent effort. Â The mechanisms for ensuring a successful project must be consistent and thorough. Â Don’t let up or get com placement. Â Hold each other accountable for commitments and assigned responsibilities. Â
Time and time again, we have seen how these principles, if followed, can lead to success. Â Yet all too often, we also see where companies try to take shortcuts in the name of tactical expediency, and fall short in their expectations for project success.
I’ll discuss more on this topic in the near future. Stay tuned. Â In the mean time, Cooperatively Execute!




 I received my first order of
I received my first order of