This afternoon, I read a recently released Verizon report, “State of the Market: Internet of Things 2016.†It provides a quick, but fascinating read about Internet of Things market forces, real-life industry adoption, key trends and real-world successes.  The report states:
The Internet of Things (IoT) is much more than the result of seemingly fragmented and complex technologies smashed together … forward-thinking business and public sector leaders, as well as consumers and developers, are turning to the Internet of Things to address some of society’s most pressing social, economic and business challenges.
Five macro trends— data monetization, consumer expectations, the regulatory landscape, network connectivity/IoT platforms and security—are helping to speed IoT adoption and deliver measurable results across several industries and sectors.
Verizon believes we just completed the year where IoT graduated from the neat new idea stage to mainstream adoption:
In our view, 2015 was the year IoT gained legitimacy. Businesses moved beyond a “start small think big†mindset. Today, they’re building IoT into future strategies and business models. Companies across all industries now have IoT squarely on their radar.
In 2015, the emphasis of startup capital began to favor enterprise focused IoT businesses over consumer applications in a big way, and the trend appears to be accelerating:
According to analysis conducted by our venture capital (VC) arm, Verizon Ventures, we estimate that consumer IoT startups raised 15% more VC funding than enterprise-focused startups in 2014. However, in 2015, roles seemed to have reversed with enterprise outpacing consumer by around 75%. In 2016, we believe the enterprise will continue that trend, but by a much larger order of magnitude—roughly 2 – 3 times more than consumer.
The sheer size of the potential IoT market continues to boggle my mind. The following chart shows a few big numbers that barely scratch the surface of the potential for IoT growth. Â

Of the many potential IoT areas of emphasis, the Verizon report specifically addresses four:
- Automotive: Connection, convergence, convenience and the connected car
- Agriculture: Farming with precision
- Smart Cities: Making communities smart and sustainable
- Energy: Providing real-time energy insight.
Of these, the closest one to my heart is Farming with Precision – quite a big step from the old farm where I grew up, where adjusting irrigation meant installing canvas dams in ditches and using a shovel to channel water down the correct rows in a field:
Industry experts have quipped that the agriculture industry is proof that soon, every company will be an IoT business.
One of the biggest trends in farming today is precision agriculture, the practice of sensing and responding to variable soil, moisture, weather and other conditions across different plots. Farmers are deploying wireless sensors and weather stations to gather real-time data about things such as how much water different plants need and whether they require pest management or fertilizer Â
Using this data, growers can customize growing processes. Indeed, one of the biggest benefits IoT offers farmers is the ability to gather much more granular data about smaller parcels of land. With site-specific data, growers can then optimize growing conditions on a plot-by-plot basis, boosting yields, improving quality and cutting costs in the process. Â
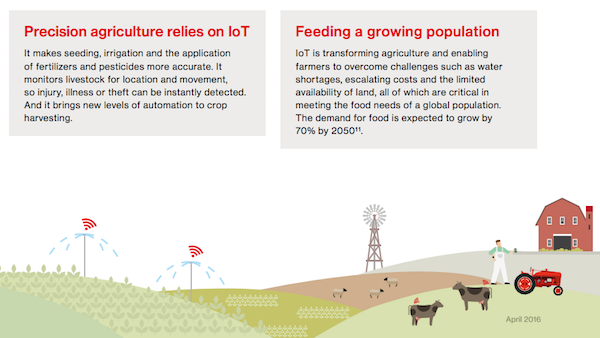
Again, the numbers are immense:
The total market size for digital precision agriculture services is expected to grow at a compound annual growth rate of 12.2% between 2014 and 2020, to reach $4.55 billion.
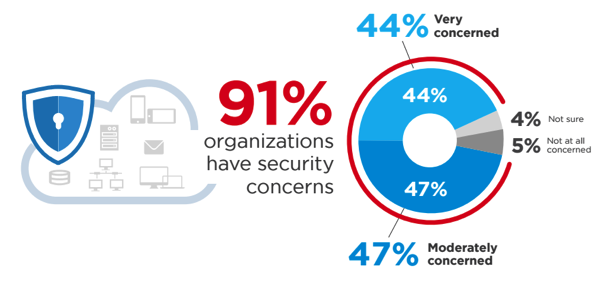
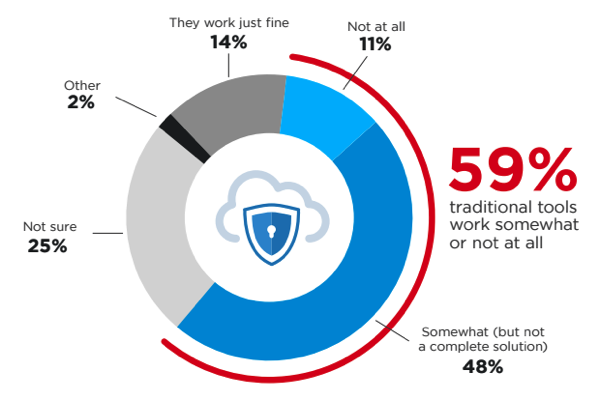
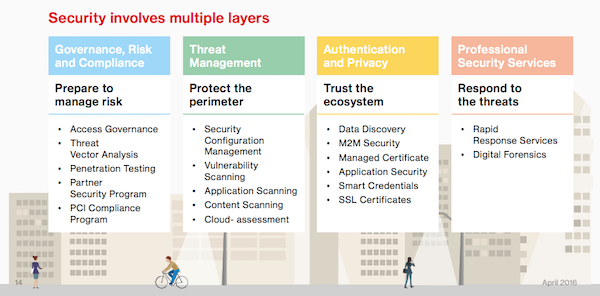
Security, is, of course, of critical importance across many facets of the IoT landscape.Â
The sheer volume of IoT devices constantly producing communications, require careful security and privacy considerations. There is no current IoT protection framework that’s ahead of the implementation of this technology. The industry is keeping up with the development of technology by looking to the rising threat vectors—some old, some new—that will impact deployments and ongoing operations. Authentication of critical data, and baseline triggers for action are the emerging security focus.
 The bottom line?
Innovation, productivity and value will thrive as private companies and the public sector both come to the inevitable conclusion that IoT is imperative to delivering the integrated, easy to use and sustainable products and services demanded by an increasingly mobile, tech-savvy 21stcentury society.
No single company or country can realize the full promise of IoT on its own. We believe collaboration, experimentation and openness will:
- Create cleaner cities
- Deliver better healthcare
- Make transportation systems safer
- Conserve water
- Boost productivity
- And make the digital world work better for consumers and citizens.
We live in an exciting world, at an exciting time. Â Hang on for the ride!