Video: Privacy and Security by Design: An Enterprise Architecture Approach
In the following video, Dr. Ann Cavoukian describes the paper I was privileged to co-author with her.
More information and a download link is available here.

In the following video, Dr. Ann Cavoukian describes the paper I was privileged to co-author with her.
More information and a download link is available here.
 Today, we are pleased to announce publication of a paper entitled “Privacy and Security by Design: An Enterprise Architecture Approach,” which I co-authored with Ann Cavoukian, Ph.D., Information & Privacy Commissioner, Ontario, Canada.
Today, we are pleased to announce publication of a paper entitled “Privacy and Security by Design: An Enterprise Architecture Approach,” which I co-authored with Ann Cavoukian, Ph.D., Information & Privacy Commissioner, Ontario, Canada.
In the foreword to the paper, Dr. Cavoukian wrote:
In an earlier paper with Oracle, we discussed the convergence of paradigms between the approach to privacy I have long championed called Privacy by Design, and a similar approach to security called ‘Security by Design.’ The current and future challenges to security and privacy oblige us to revisit this convergence and delve deeper. As privacy and security professionals, we must come together and develop a proactive approach to security – one that is indeed “by design.” To this end, I am delighted to be partnering with Mark Dixon, Enterprise Architect, Information Security, at Oracle Corporation, on this joint paper.
This paper has two key objectives:
To achieve these objectives, the paper includes the following major sections:
The conclusion states:
“In this paper, we explored the strong synergy that exists between the related disciplines of privacy and security. While on the one hand, strong security is essential to meet the objectives of privacy, on the other hand, well-known privacy principles are valuable in guiding the implementation of security systems. On the basis of this synergy, we defined a set of foundational principles for Security by Design that are modeled upon and support the foundational principles of Privacy by Design. …
“On the basis of this new Security by Design approach, we then developed an enterprise-level process for defining, governing and realizing a ‘by design’ approach to security. In order to become a reality for enterprises, Security by Design requires strong leadership and continuous goal-setting. However, Enterprise Architecture is an ongoing journey, not a single project or disjointed set of loosely related projects. Our discussion found that if an EA framework is followed to define an EA security strategy in harmony with the holistic, interdisciplinary principles of Privacy by Design and Security by Design, and if a formal governance process is implemented to guide and govern the journey, then an enterprise can be proactive, rather than reactive, in addressing any security concerns.
We hope this paper will assist enterprises to deliver stronger security and better privacy, for all of their stakeholders – a win/win proposition.
It was an honor today to be announced as a Privacy by Design Ambassador by the Information and Privacy Commissioner of Ontario, Canada:
Privacy by Design Ambassadors are an exclusive, but growing, group of privacy thought-leaders committed to ensuring the ongoing protection of personal information by following the Principles of PbD. Â Ambassadors advance the case for embedding privacy protective measures in technology, processes and physical design. …
The Information and Privacy Commissioner of Ontario (IPC) is an independent officer of the Legislature whose mandate is to oversee compliance with public sector access and privacy legislation and health sector privacy legislation in the province of Ontario.
The IPC recognizes ambassadors based on their attestations that they apply the principles of Privacy by Design. The IPC does not endorse any company or product of any recognized ambassador.
It was humbling to be listed among others whom I admire and respect for their contributions to the industry we serve.
I have deeply appreciated the opportunity to work closely with Dr. Ann Cavoukian and her staff on a soon to be announced joint paper on principles of privacy and security. Â I look forward to announcing and discussing this paper soon.
![]()
Today I read an informative paper published by GigaOM Research entitled, “The Internet of Things: A Market Landscape.”  I find The Internet of Things to be the most interesting area of technology and business in my professional world today.  This paper did an excellent job of providing an overview of the IoT landscape and highlighting both opportunities and challenges.
A few things that I found intriguing:
IoT is not just new technology:
The internet of things is not a single technology trend. Rather, it is a way of thinking about how the physical world at large and the objects, devices, and structures within it are becoming increasingly interconnected.
The market is moving rapidly to mind-boggling scale:
- Some 31 billion internet-connected devices will exist by 2020, according to Intel.
- A family of four will move from having 10 connected devices in 2012 to 25 in 2017 to 50 in 2022.
- Mobile subscriptions will exceed the number of people in the world by early 2014.
Identity is first on the list of important characteristics:
For things to be manageable, they need to be identifiable either in terms of type or as a unique entity. … Identification by type or by instance is fundamental to the internet of things.
The power of IoT comes from connectivity, not just individual components:
The internet of things is an ultra-connected environment of capabilities and services, enabling interaction with and among physical objects and their virtual representations, based on supporting technologies such as sensors, controllers, or low-powered wireless as well as services available from the wider internet.
The biggest challenges? Â Security, monitoring and surveillance:
Computer security, say the experts, boils down to protecting the confidentiality, integrity, and availability of both data and services. With the internet of things looking set to create all manner of data, from heart rate and baby monitors to building management systems, there is clearly going to be a great deal to protect. …
The internet of things enables the whole world to be monitored. …  the potential for the inappropriate use of such technologies — for example, to spy on partners or offspring — will grow. In the business context as well, the role of the internet of things offers a wealth of opportunity but also of abuse.
The bottom line? Â The possibilities are vast, the challenges daunting, but IoT is happening. Â It will be great to go along for the ride.
Yesterday, I was introduced to a recently-published 90+ page report, “The Report of the Commission on the Theft of American Intellectual Property.”
The Commission on the Theft of American Intellectual Property is an independent and bipartisan initiative of leading Americans from the private sector, public service in national security and foreign affairs, academe, and politics. The three purposes of the Commission are to:
- Document and assess the causes, scale, and other major dimensions of international intellectual property theft as they affect the United States
- Document and assess the role of China in international intellectual property theft
- Propose appropriate U. S. policy responses that would mitigate ongoing and future damage and obtain greater enforcement of intellectual property rights by China and other infringers
The members of this commission represent an interesting cross section of private and public sector leaders:
- Dennis C. Blair (co-chair), former Director of National Intelligence and Commander in Chief of the U. S. Pacific Command
- Jon M. Huntsman, Jr. (co-chair), former Ambassador to China, Governor of the state of Utah, and Deputy U. S. Trade Representative
- Craig R. Barrett, former Chairman and CEO of Intel Corporation
- Slade Gorton, former U. S. Senator from the state of Washington, Washington Attorney General, and member of the 9-11 Commission
- William J. Lynn III, CEO of DRS Technologies and former Deputy Secretary of Defense
- Deborah Wince-Smith, President and CEO of the Council on Competitiveness
- Michael K. Young, President of the University of Washington and former Deputy Under Secretary of State
The report addresses the huge scale of intellectual property theft – involving hundreds of billions of dollars and huge impact on ongoing innovation:
The scale of international theft of American intellectual property (IP) is unprecedented—hundreds of billions of dollars per year, on the order of the size of U. S. exports to Asia. The effects of this theft are twofold. The first is the tremendous loss of revenue and reward for those who made the inventions or who have purchased licenses to provide goods and services based on them, as well as of the jobs associated with those losses. American companies of all sizes are victimized. The second and even more pernicious effect is that illegal theft of intellectual property is undermining both the means and the incentive for entrepreneurs to innovate, which will slow the development of new inventions and industries that can further expand the world economy and continue to raise the prosperity and quality of life for everyone. Unless current trends are reversed, there is a risk of stifling innovation, with adverse consequences for both developed and still developing countries. The American response to date of hectoring governments and prosecuting individuals has been utterly inadequate to deal with the problem.
The report recommends several short, medium and long term remedies, including public policy, legislation, public/private cooperation and advances in cyber security technology and processes.
In the last category, I was interested to read the following observation (emphasis mine):
Even the best security systems using vulnerability-mitigation measures, including those with full-time dedicated operations centers, cannot be relied on for protection against the most highly skilled targeted hackers. A network exists in order to share information with authorized users, and a targeted hacker, given enough time, will always be able to penetrate even the best network defenses.
Effective security concepts against targeted attacks must be based on the reality that a perfect defense against intrusion is impossible. The security concept of threat-based deterrence is designed to introduce countermeasures against targeted hackers to the point that they decide it is no longer worth making the attacks in the first place. In short, it reverses the time, opportunity, and resource advantage of the targeted attacker by reducing his incentives and raising his costs without raising costs for the defender. Conceptual thinking about and effective tools for threat-based deterrence are in their infancy, but their development is a very high priority both for the U. S. government and for private companies.
The observation that “a perfect defense against intrusion is impossible,” is chilling. Â What is to be done?
The report’s recommendation to battle this challenge:
Encourage adherence to best-in-class vulnerability-mitigation measures by companies and governments in the face of an evolving cybersecurity environment. Despite their limited utility against skilled and persistent targeted hackers, computer security systems still need to maintain not only the most up-to-date vulnerability-mitigation measures, such as firewalls, password-protection systems, and other passive measures.
They should also install active systems that monitor activity on the network, detect anomalous behavior, and trigger intrusion alarms that initiate both network and physical actions immediately. This is a full-time effort. Organizations need network operators “standing watch†who are prepared to take actions based on the indications provided by their systems, and who keep a “man in the loop†to ensure that machine responses cannot be manipulated.
Organizations need to have systems—software, hardware, and staff—to take real-time action to shut down free movement around the house, lock inside doors, and immobilize attackers once the alarms indicate that an intrusion has started. Some government agencies and a few corporations have comprehensive security systems like this, but most do not.
The bottom line is that Intellectual Property espionage is a huge problem with no simple solutions. Â Technology alone cannot solve the problem. Â There are major social, political, economic and cultural challenges that must be addressed. But we in the information security business have our work cut out for us.
I like the diagram Mark O’Neill of Vordel put in a recent post, “Identity is the New Perimeter.” That phrase has been floating around for some time, but I think this diagram illustrates the concept in the simplest, clearest way I have seen:
The article does a good job of describing this new way of looking at security. Â As Mark mentioned in the post, Bill Gates once said, “security should be based on policy, not topology.”
Today, I read an interesting white paper, “Big Data in M2M: Tipping Points and Subnets of Things,” published by Machina Research. From the introduction:
This White Paper focuses on three hot topics in the TMT space currently: Big Data and the ‘Internet of Things’, both examined through the prism of machine-to-machine communications. We have grouped these concepts together, since Big Data analytics within M2M really only exists within the context of heterogeneous information sources which can be combined for analysis. And, in many ways, the Internet of Things can be defined in those exact same terms: as a network of heterogeneous devices.
The white paper does a good job of exploring the emerging trends of the Internet of Things, potential business opportunities and challenges faced.
As one could expect, “authenticity and security of different kinds of data,” was identified as a big challenge:
Big Data is about “mashing up†data from multiple sources, and delivering significant insights from the data. It is the combination of data from within the enterprise, from openly available data (for example, data made available by government agencies), from data communities, and from social media. And with every different source of data arises the issues of authenticity and security. Machina Research predicts that as a result of the need for data verification, enterprises will have a greater inclination to process internal and open (government) data prior to mashing-up with social media.
The following diagram shows the increase security risk as more data from external sources is collected and analyzed.
This yet another indicator of how Identity and Access Management will be critical in the successful evolution of the Internet of Things.
94%. Almost 100%! That is a pretty sobering statistic.  Please take a few minutes and scan the very informative info graphic at background check.org. Â
Just think. Almost all healthcare organizations – the ones we trust with our most sensitive information – are leaking data like a sieve. How does this affect you?
I read through the Ponemon Institute: 2012 Cost of Cyber Crime Study that was released last October.  The results are quite staggering:
Cyber crimes continue to be costly. We found that the average annualized cost of cyber crime for 56 organizations in our study is $8.9 million per year, with a range of $1.4 million to $46 million. In 2011, the average annualized cost was $8.4 million. This represents an increase in cost of 6 percent or $500,000 from the results of our cyber cost study published last year.
$8.9 million per year is the average. Â That’s a lot of money.
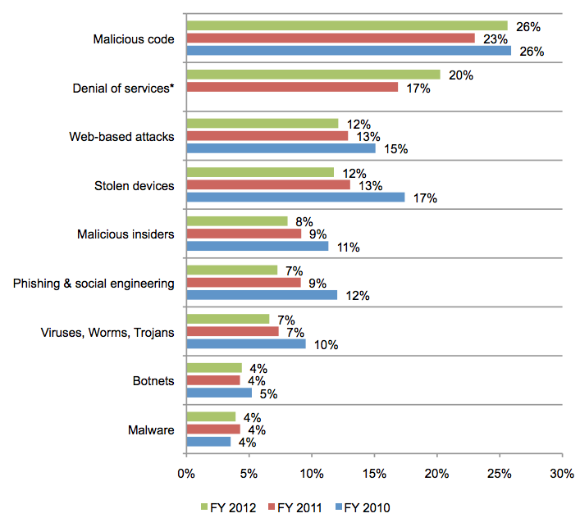
The percentage annualized cyber crime cost by attack type is shown in the following graph. Â There is a lot of bad stuff going on out there!
A great little video where Ellen DeGeneres shows a product which claims to solve all of our password problems …