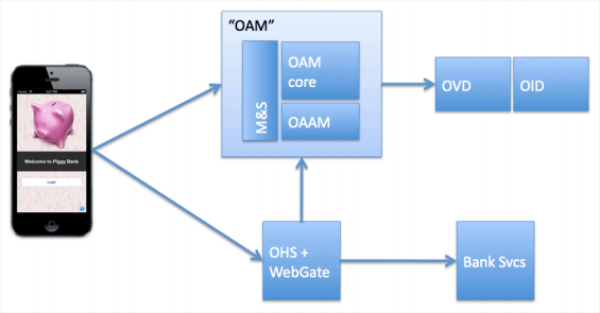
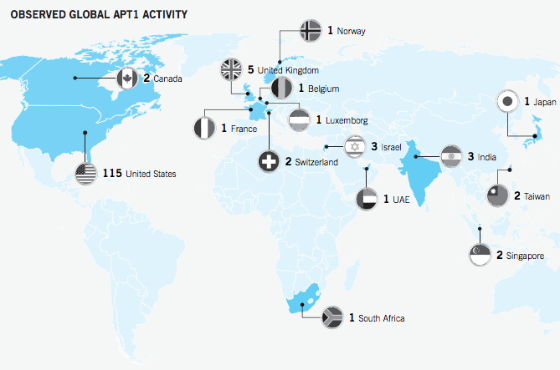
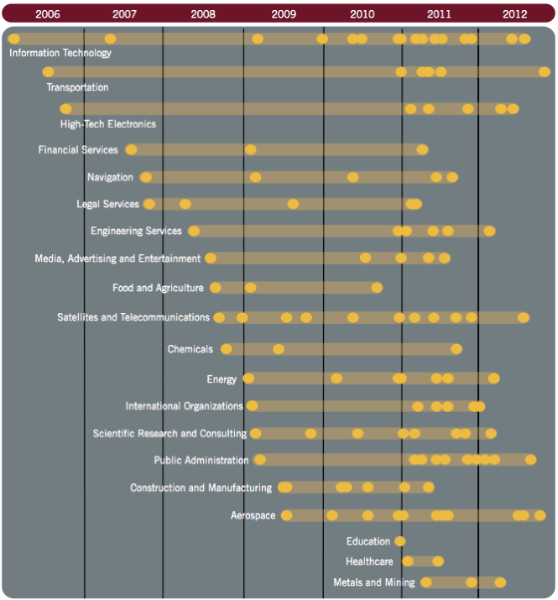
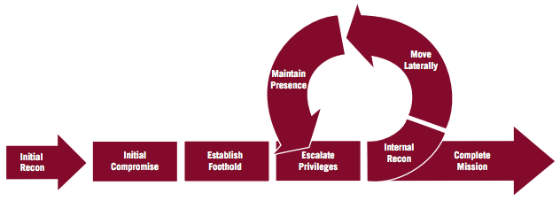
In the Oracle Information InDepth newsletter I just received, a new white paper, “Privacy and Security by Design: A Convergence of Paradigms,” was announced. The paper is a collaboration of Ann Cavoukian, Ph.D., Information and Privacy Commissioner, Ontario, Canada, and Marc Chanliau, Director, Product Management, Oracle Corporation.
The forward by Ms. Cavoukian includes this statement:
My hope is that privacy and security – by design, will continue to evolve into an essential component of information technologies and operational practices of organizations, as well as becoming an integral part of entire systems of data governance and privacy protection.
The paper further explains the value of these converging topics:
This paper highlights the convergence of these two paradigms. In the first part, the concept of security by design as understood in the technical community is introduced. In the second, the concept of Privacy by Design (PbD) as understood in the privacy community is discussed. The third and final part explores how these two concepts share notable similarities and how they may complement and mutually reinforce each other.
The paper provides a good overview of Security by Design …
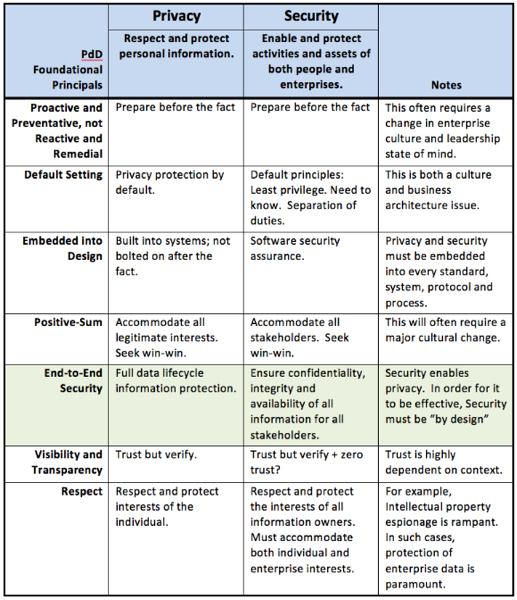
… we address three aspects of security by design: i) software security assurance (designing software systems that are secure from the ground up and minimizing the impact of system breach when a security vulnerability is discovered) ; ii) preserving privacy in the enterprise environment and; iii) ensuring identity across heterogeneous vendors.
… and Privacy by Design.
Privacy by Design … is aimed at preventing privacy violations from arising in the first place. PbD is based on seven (7) Foundational Principles. It emphasizes respect for user privacy and the need to embed privacy as a default condition. It also preserves a commitment to functionality in a doubly-enabling ‘win-win, ’ or positive-sum strategy. This approach transforms consumer privacy issues from a pure policy or compliance issue into a business imperative.
The paper concludes:
It is becoming widely recognized that privacy and security must both be embedded, by default, into the architecture, design and construction of information processes. This is a central motivation for PbD, which is aimed at reducing the risk of a privacy harm from arising in the first place. By taking a proactive approach, it is possible to demonstrate that it is indeed possible (and far more desirable) to have privacy and security! Why settle for one when you can have both?
I found the paper to be thoughtful and timely. By coincidence, this morning I committed to an event next week where I will meet Ms. Cavoukian. I look forward to it!