Cloud Computing,
Information Security
Author:
Mark Dixon
Tuesday, September 11, 2012
4:47 am
 When I was in 7th grade, I played the trombone in the Gooding, Idaho, Jr. High band – or at least tried to play it. Once, we participated in a music festival where I played a solo rendition of the soaring anthem, “Jerusalem,” in front of a judge. When I finished the piece, she remarked, “the trombone can be a beautiful instrument.” I was devastated of course, and was somewhat relieved to hang up my trombone, so to speak, when we moved to a tiny town without a band the next year.
When I was in 7th grade, I played the trombone in the Gooding, Idaho, Jr. High band – or at least tried to play it. Once, we participated in a music festival where I played a solo rendition of the soaring anthem, “Jerusalem,” in front of a judge. When I finished the piece, she remarked, “the trombone can be a beautiful instrument.” I was devastated of course, and was somewhat relieved to hang up my trombone, so to speak, when we moved to a tiny town without a band the next year.
I was reminded of that incident this morning when I read a Mashable article, “Top 5 Misconceptions about the Cloud,” sponsored by Western Digital. The fifth “misconception” was “You Can’t Beef Up Security on the Cloud.” In my mind’s eye, I could almost see my trombone judge saying, “The cloud can be a secure place.”
So what’s the problem? Much like a 7th grader’s ill-conceived belief that he could impress a judge with little practice and poor technique, the article’s overly simplistic recommendation for bolstering cloud security was “You can use behavior-based key management servers and encryption key management to give your files an extra layer of protection.”
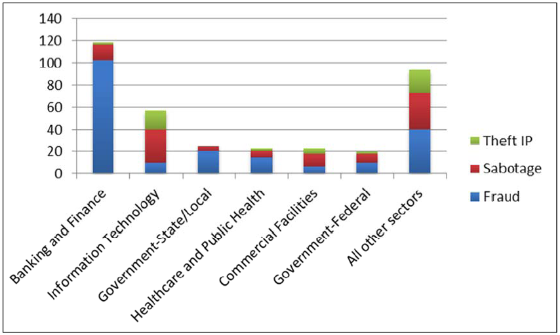
Cloud security entails much, much more than that.
I can accept that cloud based solutions can be well-secured, but we must not be complacent or expect great results with little effort.
 My Dad once told me, “If you keep your eyes and ears open, you’ll learn something new every day.”
My Dad once told me, “If you keep your eyes and ears open, you’ll learn something new every day.”