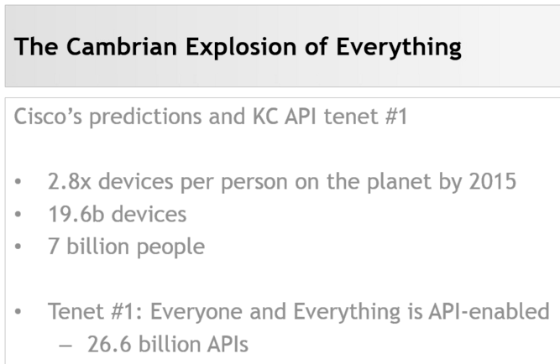
Enabling Digital Transformation with REST API
I was recently introduced to a powerful new tool created by the folks at Persistent Systems, a long time Oracle development and systems integrator partner. The Oracle Identity and Access Management platform has a very rich set of Java APIs that enable developers to access nearly all of the functionality this platform from external applications.  The challenge is not completeness, but complexity.  To take advantage of this rich API set, external developers have to know much about the internal workings of the IAM products and the intricacies of writing the Java code to access the APIs.
The Persistent Systems engineers have developed a REST API on top of the Oracle Identity Governance Java API that exposes OIG capabilities in a much simpler, more “process friendly†way. For example, a few services available are:
- User Access Request
- Get User’s Provisioned Roles
- Acting on Pending Authorizations
- Authenticate User
- Authorize User
… and the list goes on.
How would you like to translate those “business level†requests into Java API calls?
To demonstrate the capability of the REST API, a developer at Persistent Systems created the application shown in the image below, with a clean, easy-to use interface for OIG approvals and certifications – all without being an expert in Java or the detailed processes within OIG. Â The iPhone and Apple watch images include screen shots from my phone and watch. Â It really does work!
The most important thing to consider is not the neat user interface – although it has some cool features – it is how an intelligently constructed REST API can provide development agility, application flexibility and rapid deployment, all essential enablers for digital transformation.
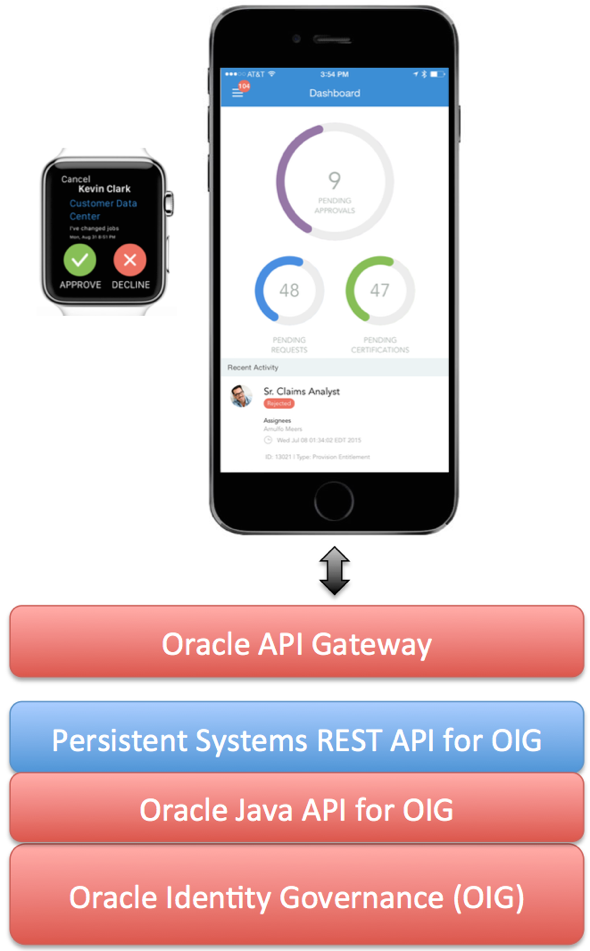
 Leonardo Da Vinci has been credited with the wise statement, “Simplicity is the ultimate sophistication.† I think Leonardo would like this approach.