Google Mobile Backend Starter: AuthN and AuthZ in the Cloud
Of the many articles I read today, which one piqued my interest the most? “Google Launches Mobile Backend Starter, A One-Click Deployable Cloud Backend For Android Apps.”
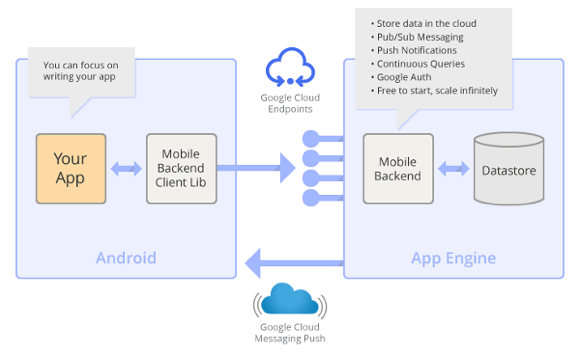
Mobile Backend Starter provides developers with a one-click deployable mobile backend and a client-side framework for Android that provides them with storage services, access to Google Cloud Messaging, continuous queries and Google’s authentication and authorization features. (emphasis mine)
Â
Why is this important? Â I can think of at least 4 reasons:
- If this is the easiest way for developers to embed authentication and authorization functionality into their apps, guess which method they will choose?
- If it is easy to exploit back end services from mobile apps, emerging apps will ail be richer in functionality and content, because app developers will focus on real application innovation, rather than re-inventing the AuthN/AuthZ wheel.
- Google’s quest to become Identity Provider for the world just took a big step forward. Â If app developers can easily rely on Google AuthN/AuthZ, other companies that aspire to be IDPs will be playing catch up.
- This pattern of easy-to-use backend infrastructure available to developers could revolutionize application development as we know it – not just mobile apps.
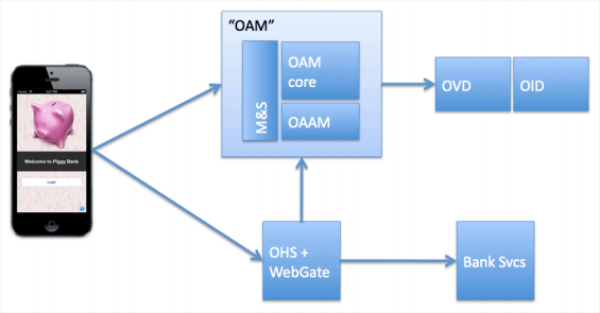
The obvious question is “where are you, Apple?” Â But a bigger question is for all of us engaged in enterprise IAM, “how will we quickly adapt to this model?”