Cloutage.org – Cloud Incidents, News, Resources
Thanks to my colleague Simon Thorpe for pointing out Cloutage.org, a website which provides up to date information about outages and security incidents in public cloud computing:
â€Cloutage exists to empower organizations by providing cloud security knowledge and resources so that they may properly assess information security risks. The project aims to document known and reported incidents with cloud services while also providing a one-stop shop for cloud security news and resources.â€
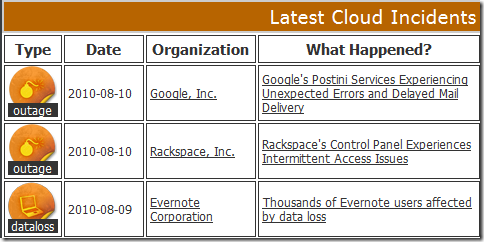
The Cloutage home page shows this a list of “Latest Cloud Incidentsâ€: Here are the most recent three:
I was particularly interested in the Evernote data loss, because I am a heavy Evernote user. I don’t think I lost anything, but it makes me rather nervous – and thankful for the local repository of everything stored in the Evernote cloud.
I suppose the message this brings most strongly home to me is this: Cloud Computing is not invulnerable. Our trust in cloud computing must be based on solid evidences of sufficient information security. We must demand (and, as security professionals help enable) auditable security technology and processes in cloud computing.