KuppingerCole: Information Security Predictions and Recommendations 2014
Author: Mark Dixon
Thursday, December 19, 2013
2:53 pm

Kuppinger Cole just released an insightful Advisory Note: “Information Security Predictions and Recommendations 2014.”  The introduction stated:
Information Security is in constant flux. With the changing threat landscape, as well as a steary stream of new innovations, demand for Information Security solutions is both growing and re-focusing.
I like both the predictions and recommendations in this report. Â Here are a few excerpts from my favorite recommendations:
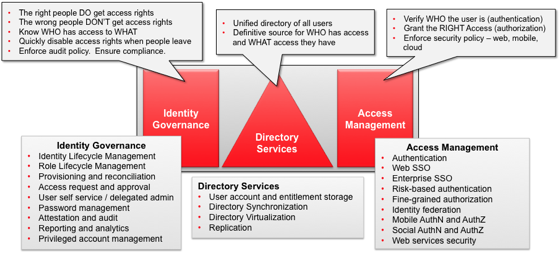
Cloud IAM (Identity and Access Management)
Define an IAM strategy for dealing with all types of users, devices, and deployment models that integrates new Cloud IAM solutions and existing on-premise IAM seamlessly.
API Economy
Before entering this brave, new world of the API “Economyâ€, define your security concept first and invest in API Security solutions. Security can’t be an afterthought in this critical area.
IoEE (Internet of Everything and Everyone)
Before starting with IoEE, start with IoEE security. IoEE requires new security concepts, beyond traditional and limited approaches.
Ubiquitous Encryption
Encryption only helps when it is done consistently, without leaving severe gaps.
The whole paper is well worth reading. Â Hopefully, this post whetted your appetite a little bit.