Identity and Access Management – Capability Model
In a recent twitter conversation with Andre Koot, he suggested that we needed innovation in both Identity Management and Access Management. Â He referred me to his blog, entitled “Let’s Kill the IAM Acroynm.” Â Andre suggested:
Identity Management is a process for managing the lifecycle of identities … Access Control is a whole different ballgame …
After reading his blog, it occurred to me that he and I defined those two terms a bit differently. Â I promised Andre that I would blog about it.
The diagram below shows how we at Oracle talk about the broad area of Identity and Access Management – encompassing three general areas:
- Identity Governance is about making sure the right people are granted the right access rights and making sure the wrong ones aren’t
- Access Management is about enforcing those access rights, within specified policy, when users attempt to access a desire application or system
- Directory Services provides ways to control where identity information about users and accessed rights are stored.
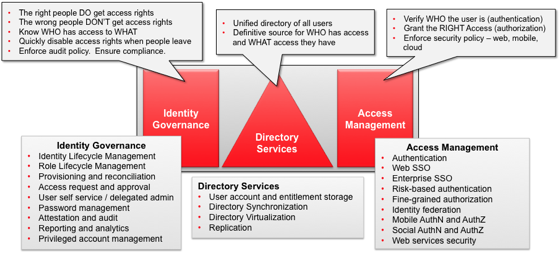
Does this provide the right demarcation between the various functional areas? Â It seems to resonate well with our customers, and provides a valuable model to aid communications. Â I’d be happy to hear any feedback you have.
By the way, this diagram is more effective as a PowerPoint build slide. Â Let me know and I’d be happy to send you a copy.








