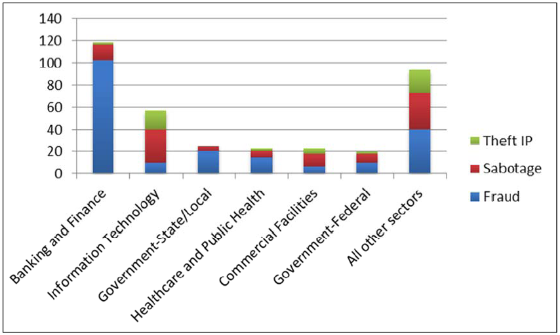
Mandiant Report: APT1 – Exposing One of China’s Cyber Espionage Units
![]()
Mandiant, an American cyber security firm, recently released a 74 page report documenting evidence of cyber attacks by the People’s Liberation Army of the Republic of China:
Since 2004, Mandiant has investigated computer security breaches at hundreds of organizations around the world. The majority of these security breaches are attributed to advanced threat actors referred to as the “Advanced Persistent Threat†(APT). … this report is focused on the most prolific of these groups. We refer to this group as “APT1†and it is one of more than 20 APT groups with origins in China. APT1 is a single organization of operators that has conducted a cyber espionage campaign against a broad range of victims since at least 2006. From our observations, it is one of the most prolific cyber espionage groups in terms of the sheer quantity of information stolen. …
APt1 has systematically stolen hundreds of terabytes of data from at least 141 organizations, and has demonstrated the capability and intent to steal from dozens of organizations simultaneously. APT1 has a well-defined attack methodology, honed over years and designed to steal large volumes of valuable intellectual property. Once APT1 has established access, they periodically revisit the victim’s network over several months or years and steal broad categories of intellectual property, including technology blueprints, proprietary manufacturing processes, test results, business plans, pricing documents, partnership agreements, and emails and contact lists from victim organizations’ leadership.
This detailed report includes a map showing observed APT1 activity …
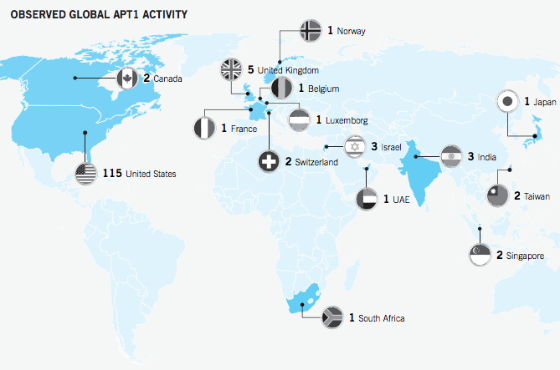
Â
… and a timeline of observed compromises by industry sector:
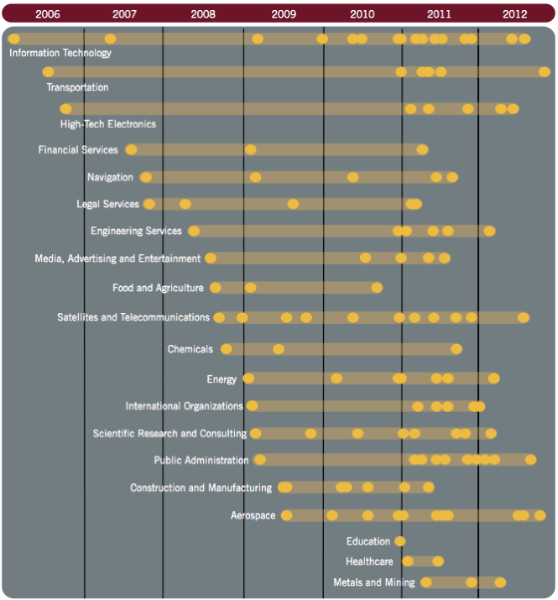
Â
The report includes a detailed analysis of the APT attack lifecycle and methods for compromising the systems in the targets they attacked:
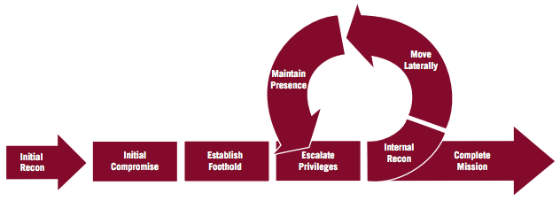
Detailed background about  the infrastructure used in the attacks and some of the people involved in this work are also included.
The report concludes:
In a State that rigorously monitors Internet use, it is highly unlikely that the Chinese Government is unaware of an attack group that operates from the Pudong New Area of Shanghai. The detection and awareness of APT1 is made even more probable by the sheer scale and sustainment of attacks that we have observed and documented in this report. Therefore the most probable conclusion is that APT1 is able to wage such a long-running and extensive cyber espionage campaign because it is acting with the full knowledge and cooperation of the government. Given the mission, resourcing, and location of PLA Unit 61398, we conclude that PLA Unit 61398 is APT1.
Perhaps this statement from Sun Tzu, in his book, The Art of War, is particularly appropriate in this case:
If you know the enemy and know yourself, you need not fear the result of a hundred battles. If you know yourself but not the enemy, for every victory gained you will also suffer a defeat. If you know neither the enemy nor yourself, you will succumb in every battle.