Source Doc: NIST Computer Security Division Annual Report
 The National Institute of Standards and Technology (NIST) has released its 2010 Computer Security Division Annual Report. Donna Dodson, Chief, Computer Security Division & Deputy Chief Cybersecurity Advisor offers the following in her welcome statement:
The National Institute of Standards and Technology (NIST) has released its 2010 Computer Security Division Annual Report. Donna Dodson, Chief, Computer Security Division & Deputy Chief Cybersecurity Advisor offers the following in her welcome statement:
The Computer Security Division (CSD), a component of NIST’s Information Technology Laboratory (ITL), conducts research, development and outreach necessary to provide standards and guidelines,  tools, metrics and practices to protect our nations information and  communication infrastructure.
In fiscal year (FY) 2010, CSD continued to build on its work in security management and assurance, cryptography and systems security, identity management and emerging security technologies.  CSD played a vital role in both national and international security  standard setting.  The division continues its leadership role in technologies and standards for Cloud Computing, Identity Management and as a Government Wide Leader and national coordinator  for the National Initiative for Cybersecurity Education (NICE).  In addition, this year marked the publication of NIST Interagency Report  (NISTIR) 7628,  Guidelines for Smart Grid Security, which identifies  security requirements applicable to the Smart Grid, security-relevant use cases, logical interface diagrams and interface categories,  vulnerability classes abstracted from other relevant cyber security  documents, specific issues applicable to the Smart Grid, and privacy concerns. We also continued to provide reference specifications  in multiple areas, allowing others to leverage our work to increase  the security of their systems and products.
…
Looking forward to FY2011, CSD plans to continue its work in information security, producing standards, guidelines, technical reference materials and specifications to improve the information security management of systems across the Nation and around the  world.
By the way, this report has the coolest front cover of any government report in recent history.  The image shown above is but a small excerpt.  Not that this has anything to do with the contents of the report or anything …



 Cyberwarzone.com
Cyberwarzone.com When I hear a message that begins, “We’re from the government, and we’re here to help,” I am naturally suspicious. My political philosophy, based on personal freedom, individual responsibility and natural consequences, is all too often infringed upon by over-reaching, even if well-intentioned, government mandates. So, when I first learned of the “
When I hear a message that begins, “We’re from the government, and we’re here to help,” I am naturally suspicious. My political philosophy, based on personal freedom, individual responsibility and natural consequences, is all too often infringed upon by over-reaching, even if well-intentioned, government mandates. So, when I first learned of the “ Where are
Where are 
 The recent security breach affecting Sony Corp’s PlayStation network, is receiving high profile attention. As reported by Nick Wingfield in today’s
The recent security breach affecting Sony Corp’s PlayStation network, is receiving high profile attention. As reported by Nick Wingfield in today’s  Today, in a Computerworld article entitled, “
Today, in a Computerworld article entitled, “ I first read the news about Apple’s secretive location tracking capability in the Kaspersky Labs Threat Post article, “
I first read the news about Apple’s secretive location tracking capability in the Kaspersky Labs Threat Post article, “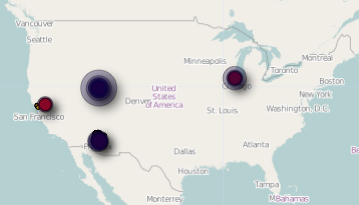
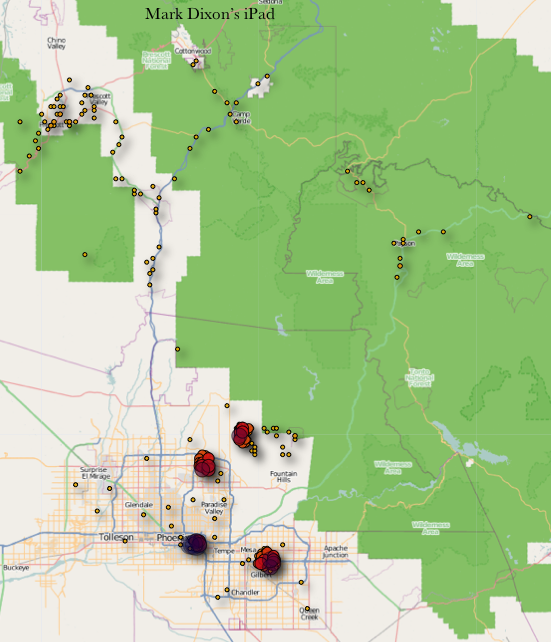
 I am anxious for the time when I can buy groceries or pay for a meal with my iPhone. According to Juniper Research, that time may be be closer than you would think.
I am anxious for the time when I can buy groceries or pay for a meal with my iPhone. According to Juniper Research, that time may be be closer than you would think.