May 25, 2018 is bearing down on us like a proverbial freight train. That is the date when the European Union General Data Protection Regulation (GDPR) becomes binding law on all companies who store or use personal information related to EU citizens. (Check out the count down clock on the GDPR website).
Last week, Oracle published a new white paper, “Helping Address GDPR Compliance Using Oracle Security Solutions.”
Leveraging our experience built over the years and our technological capabilities, Oracle is committed to help customers implement a strategy designed to address GDPR security compliance. This whitepaper explains how Oracle Security solutions can be used to help implement a security framework that addresses GDPR.
GDPR is primarily focused on protecting fundamental privacy rights for individuals. By necessity, protection of personal information requires good data security. As stated in the white paper,Â
The protection of the individuals whose personal data is being collected and processed is a fundamental right that necessarily incorporates IT security.
In modern society, IT systems are ubiquitous and GDPR requirements call for good IT security. In particular, to protect and secure personal data it is, among other things, necessary to:
- Know where the data resides (data inventory)
- Understand risk exposure (risk awareness)
- Review and, where necessary, modify existing applications (application modification)
- Integrate security into IT architecture (architecture integration)
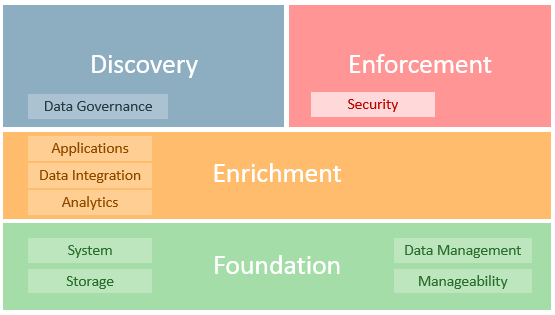
Oracle proposes the following framework toÂ
… help address GDPR requirements that impact data inventory, risk awareness, application modification, and architecture integration. The following diagram provides a high-level representation of Oracle’s security solutions framework, which includes a wide range of products and cloud services.
Â
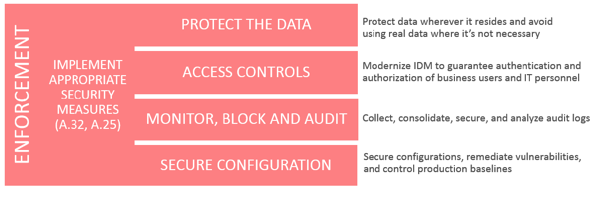
The paper primarily focuses on the “Enforcement†portion of this model, postposing that:
… four security requirements are a part of many global regulatory requirements and well-known security best practices (i.e. ISO 27000 family of standards, NIST 800-53, PCI-DSS 3.2, OWASP and CIS Controls).
In conclusion, the paper states:
The path towards GDPR compliance includes a coordinated strategy involving different organizational entities including legal, human resources, marketing, security, IT and others. Organizations should therefore have a clear strategy and action plan to address the GDPR requirements with an eye towards the 25 May, 2018 deadline.
Based on our experience and technological capabilities, Oracle is committed to help customers with a strategy designed to achieve GDPR security compliance.
Â
May 25, 2018 is less than ten short months away. Â We all have a lot of work to do.
Â
Â
Â