Gigabytes of Personal Data
Now, in honor of my post about Personal Clouds – the philosophy of Frank & Ernest:

Now, in honor of my post about Personal Clouds – the philosophy of Frank & Ernest:
Last Thursday, I participated in the Privacy Tweet Chat led by @OracleIDM, featuring Dr. Ann Cavoukian, Information and Privacy Commissioner of Ontario Canada, tweeting as @embedprivacy.  The #PrivQA chat archive is available now on Storify.
I always enjoy these tweet chats, and invariably learn more than I contribute. Â Perhaps the key insight I gained in this chat is summarized in this tweet that I posted later in the chat:
Privacy is freedom to decide how my data is used. Security is the mechanism to enable and protect that freedom of choice. #PrivQA
Â
The most intriguing thing to hit my desk today was the announcement of the new Mammoth service to “save links, add notes, and selectively grab content from multiple webpages into a single, shareable, organizable document.”Â
I followed a tweet from @paulmadsen and reserved my name.  You can reserve your name, too, by clicking here, or on the image below.  If you click here and reserve your name, you will be in line to use the service, and I will be one step closer to getting my account activated (I need a couple more friends to click through). We will both be one step closer to testing how to collaborate on Mammoth.  Thanks for clicking!
I do think these guys understand privacy. Â See below the image for more …
I like the sound of what they say about security and privacy:
security and privacy are top of our list …
We want to make sure nothing gets leaked unless you specifically expose it to the world. So no, no social networks to login, no weird permissions to manage, no scary dreams of that weird things you like making it out into the world. Its just simple. …
Our entire business is based on your trust – why would we screw with that? To put simply, we don’t have any reason to misuse any information we collect. And we only capture data thats needed to enable a feature for you, nothing else.
Could this be a “personal cloud” that I can really use?  It has my name on it.  It sounds like it will be secure. I look forward to checking it out. Â

After reading the white paper, “Privacy and Security by Design, A Convergence of Paradigms,” this week, I pinged a couple of associates on Twitter to see what they thought about Privacy by Design.  Steve Wilson replied to the effect that “We need more than principles.  We need implementable requirements.”
When I met with Ann Cavoukian yesterday, I asked her about that viewpoint.  She agreed that we need to step beyond principles to requirements to implementation.  She gave me a copy of a paper published last December by the PdB team, entitled, “ Operationalizing Privacy by Design: A Guide to Implementing Strong Privacy Practices.”  This paper doesn’t provide all the answers, but begins to explore how privacy is being implemented in 9 application area:
Interestingly enough, when Marc Chanliau shared with me a his unpublished report from which came the security content for the “Privacy and Security by Design” paper, it was gratifying to see the title he had selected for that larger report: “Requirements for Enterprise Security.”
There is much to do, but progress is being made.
Today I had the privilege of having lunch with Dr. Ann Cavoukian, Information and Privacy Commissioner of Ontario, Canada, along with Jack Crail, Oracle Director of Security Sales Consulting for the Western US.  It was a pleasure to have a delightful lunch, sitting outside in the deliciously warm springtime air in Scottsdale, AZ.  We explored many topics of mutual interest, but focused primarily on the concepts in the white paper, “Privacy and Security by Design, A Convergence of Paradigms,” published recently by Dr. Cavoukian and Marc Chanliau, Director, Product Management with Oracle.
I had prepared the following matrix which shows remarkably close alignment with the seven foundational principles of Privacy by Design and how these principles could also apply to Information Security. Â We recognize that the scope of security is broader than privacy, but the needs to proactively build security into all the technology and processes we create are remarkably similar.
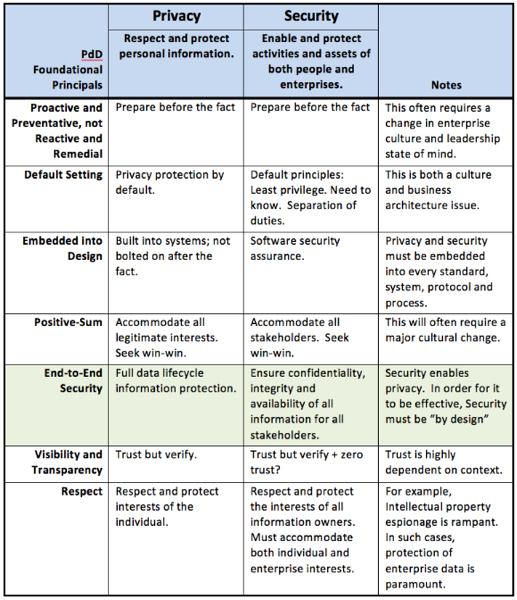
In this matrix, row 5 (End-to-end security) shows where security and privacy interact. Â In fact, end-to-end security is a necessary enabler for privacy. Â The other rows begin to explore how a Security by Design approach can align with and support Privacy by Design.
While this matrix is just in draft form, I believe it can help us discuss how  the goals and solutions of privacy and security can be aligned in a meaningful way. Â
If any on you would like to offer any suggestions for improvements, please let me know.

An interesting new report came to my attention today, “ Unlocking the Value of Personal Datra: From Collection to Usage,” published by the World Economic Forum, prepared in collaboration with The Boston Consulting Group.
Some statements from the executive summary that I like include:
Our world is changing. It is complex, hyperconnected, and increasingly driven by insights derived from big data. And the rate of change shows no sign of slowing.
… the economic and social value of big data does not come just from its quantity. It also comes from its quality – the ways in which individual bits of data can be interconnected to reveal new insights with the potential to transform business and society.
… fully tapping that potential holds much promise, and much risk.
… It is up to the individuals and institutions of various societies to govern and decide how to unlock the value – both economic and social – and ensure suitable protections
The report is organized as follows
It is particularly interesting to me that although there are numerous examples about the potential benefits of big data, there are huge challenges, and no easy fixes. Â But the report is well written and provocative. Â Well worth the time to read.
Plus as an added bonus, the report has some great pictures and graphics – a treat seldom seen in a report like this. Â Here is my favorite – it seems to capture the spirit of the crazy world of privacy and security we are in right now.
Â
In the Oracle Information InDepth newsletter I just received, a new white paper, “Privacy and Security by Design: A Convergence of Paradigms,” was announced. The paper is a collaboration of Ann Cavoukian, Ph.D., Information and Privacy Commissioner, Ontario, Canada, and Marc Chanliau, Director, Product Management, Oracle Corporation.
The forward by Ms. Cavoukian includes this statement:
My hope is that privacy and security – by design, will continue to evolve into an essential component of information technologies and operational practices of organizations, as well as becoming an integral part of entire systems of data governance and privacy protection.
The paper further explains the value of these converging topics:
This paper highlights the convergence of these two paradigms. In the first part, the concept of security by design as understood in the technical community is introduced. In the second, the concept of Privacy by Design (PbD) as understood in the privacy community is discussed. The third and final part explores how these two concepts share notable similarities and how they may complement and mutually reinforce each other.
The paper provides a good overview of Security by Design …
… we address three aspects of security by design: i) software security assurance (designing software systems that are secure from the ground up and minimizing the impact of system breach when a security vulnerability is discovered) ; ii) preserving privacy in the enterprise environment and; iii) ensuring identity across heterogeneous vendors.
… and Privacy by Design.
Privacy by Design … is aimed at preventing privacy violations from arising in the first place. PbD is based on seven (7) Foundational Principles. It emphasizes respect for user privacy and the need to embed privacy as a default condition. It also preserves a commitment to functionality in a doubly-enabling ‘win-win, ’ or positive-sum strategy. This approach transforms consumer privacy issues from a pure policy or compliance issue into a business imperative.
The paper concludes:
It is becoming widely recognized that privacy and security must both be embedded, by default, into the architecture, design and construction of information processes. This is a central motivation for PbD, which is aimed at reducing the risk of a privacy harm from arising in the first place. By taking a proactive approach, it is possible to demonstrate that it is indeed possible (and far more desirable) to have privacy and security! Why settle for one when you can have both?
I found the paper to be thoughtful and timely. By coincidence, this morning I committed to an event next week where I will meet Ms. Cavoukian. I look forward to it!

Nishant Kaushik’s tweet today prompted some paranoid thoughts about the use of big data analytics.
Scary #Privacy News Day: Raytheon RIOT – http://t.co/FB4dsnjv AND Equifax selling Employer shared employee data – http://t.co/HZSeqN9E
The first article, “Software that tracks people on social media created by defense firm,” explored how Raytheon has developed a system to track us all:
A multinational security firm has secretly developed software capable of tracking people’s movements and predicting future behaviour by mining data from social networking websites. …
“Riot is a big data analytics system design we are working on with industry, national labs and commercial partners to help turn massive amounts of data into useable information to help meet our nation’s rapidly changing security needs.”
The second article, “Your employer may share your salary, and Equifax might sell that data,” stated:
The Equifax credit reporting agency, with the aid of thousands of human resource departments around the country, has assembled what may be the most powerful and thorough private database of Americans’ personal information ever created, containing 190 million employment and salary records covering more than one-third of U.S. adults.
These two articles triggered thoughts about Axciom …
[Axciom] peers deeper into American life than the F.B.I. or the I.R.S., or those prying digital eyes at Facebook and Google. If you are an American adult, the odds are that it knows things like your age, race, sex, weight, height, marital status, education level, politics, buying habits, household health worries, vacation dreams — and on and on. …
Few consumers have ever heard of Acxiom. But analysts say it has amassed the world’s largest commercial database on consumers — and that it wants to know much, much more. Its servers process more than 50 trillion data “transactions†a year. Company executives have said its database contains information about 500 million active consumers worldwide, with about 1,500 data points per person. That includes a majority of adults in the United States.    Â
… and Lexis Nexis:
LexisNexis … is the largest data-broker in the world. They create vast profiles on people and use that information to create various reports that they sell to companies of all kinds. These reports are used to make decisions about renting, insurance and more. In the past these reports have been purchased by law enforcement and criminal organizations; all to find out more information about you.
Are there legitimate uses for all this data? Yes. Â But is there potential for illicit exploitation and mis-use of that data? Â I’d bet my bottom dollar on it. Â The unintended consequences of amassing all this personal data are what worry me.
 I read a chilling article in the Wall Street Journal this evening, entitled, “U.S. Terrorism Agency to Tap a Vast Database of Citizens.”
I read a chilling article in the Wall Street Journal this evening, entitled, “U.S. Terrorism Agency to Tap a Vast Database of Citizens.”
Yep … that means you and me – data about us law abiding citizens will now be analyzed by government officials, all without judicial warrant or probable cause.
Counterterrorism officials wanted to create a government dragnet, sweeping up millions of records about U.S. citizens—even people suspected of no crime. …
The rules now allow the little-known National Counterterrorism Center to examine the government files of U.S. citizens for possible criminal behavior, even if there is no reason to suspect them. …
Now, NCTC can copy entire government databases—flight records, casino-employee lists, the names of Americans hosting foreign-exchange students and many others. The agency has new authority to keep data about innocent U.S. citizens for up to five years, and to analyze it for suspicious patterns of behavior.
It was way back in my high school days when I read and was terrified by the prospects of George Orwell‘s novel Nineteen Eighty Four. Orwell might have predicted the wrong year, but what once seemed like far-fetched political satire seems disturbingly like accurate prophesy.
 An interesting observation in Joel Brenner’s book, “America the Vulnerable.”
An interesting observation in Joel Brenner’s book, “America the Vulnerable.”
The overlapping and ever-expanding appetite of government and commerce to keep tabs on us— and our own appetite for keeping tabs on one another— means that it’s virtually impossible to elude our own autobiographical trail of purchasing habits, property ownership, employment history, credit scores, educational records, and in my case, a security clearance record a mile long.
What have you added to your trail today? Are you sure you wanted to do that?