Information Security,
Privacy
Author:
Mark Dixon
Monday, September 23, 2013
6:28 am
 Today, we are pleased to announce publication of a paper entitled “Privacy and Security by Design: An Enterprise Architecture Approach,” which I co-authored with Ann Cavoukian, Ph.D., Information & Privacy Commissioner, Ontario, Canada.
Today, we are pleased to announce publication of a paper entitled “Privacy and Security by Design: An Enterprise Architecture Approach,” which I co-authored with Ann Cavoukian, Ph.D., Information & Privacy Commissioner, Ontario, Canada.
In the foreword to the paper, Dr. Cavoukian wrote:
In an earlier paper with Oracle, we discussed the convergence of paradigms between the approach to privacy I have long championed called Privacy by Design, and a similar approach to security called ‘Security by Design.’ The current and future challenges to security and privacy oblige us to revisit this convergence and delve deeper. As privacy and security professionals, we must come together and develop a proactive approach to security – one that is indeed “by design.” To this end, I am delighted to be partnering with Mark Dixon, Enterprise Architect, Information Security, at Oracle Corporation, on this joint paper.
This paper has two key objectives:
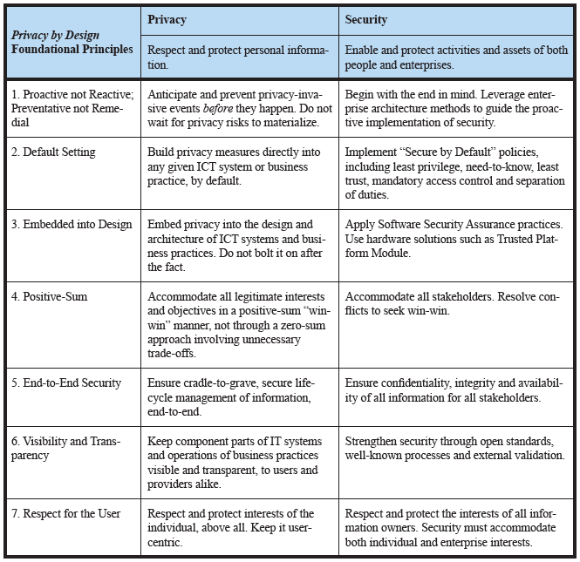
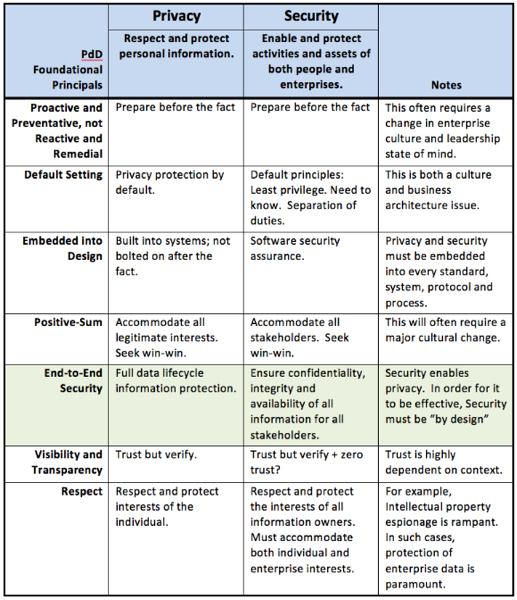
- Define a set of foundational “Security by Design†principles that are modelled upon and support the 7 foundational principles of Privacy by Design.
- Illustrate an enterprise-level process for defining and governing the strategic journey of Security by Design through an enterprise architecture approach.
To achieve these objectives, the paper includes the following major sections:
- Foundational Principles of Privacy by Design
- Foundational Principles of Security by Design
- The Enterprise Security Journey
- Conclusion
The conclusion states:
“In this paper, we explored the strong synergy that exists between the related disciplines of privacy and security. While on the one hand, strong security is essential to meet the objectives of privacy, on the other hand, well-known privacy principles are valuable in guiding the implementation of security systems. On the basis of this synergy, we defined a set of foundational principles for Security by Design that are modeled upon and support the foundational principles of Privacy by Design. …
“On the basis of this new Security by Design approach, we then developed an enterprise-level process for defining, governing and realizing a ‘by design’ approach to security. In order to become a reality for enterprises, Security by Design requires strong leadership and continuous goal-setting. However, Enterprise Architecture is an ongoing journey, not a single project or disjointed set of loosely related projects. Our discussion found that if an EA framework is followed to define an EA security strategy in harmony with the holistic, interdisciplinary principles of Privacy by Design and Security by Design, and if a formal governance process is implemented to guide and govern the journey, then an enterprise can be proactive, rather than reactive, in addressing any security concerns.
We hope this paper will assist enterprises to deliver stronger security and better privacy, for all of their stakeholders – a win/win proposition.